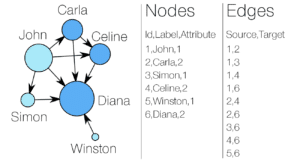
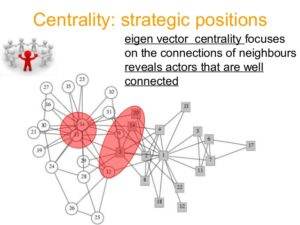
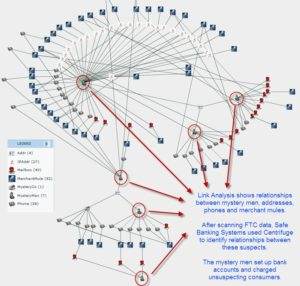
DHS Publicly Admits to Social Media Investigations Since 2015
DHS announced through this OIG Report 17-40 that it began Social Media Investigation Pilots in December 2015. This does not mean DHS just began Social Media Investigations. The OIG report simply states that DHS, as an agency, began formalizing the process of Social Media Investigations in late 2015.
For immigration advocates and aliens (non U.S. Citizens) this Report signals that the New Administration will shortly require all aliens, even Green Card Holders, to provide all their social media credentials to include user names and passwords. I am quite sure every I-94 Kiosk will soon require even 20 year Lawful Permanent Residents returning to their homes in the U.S. to enter all social media credentials or be refused boarding.
From 2014-social-media-use-in-law-enforcement LEXIS NEXIS
As the reader notes from the historical posts below, DHS has long been conducting Social Media Investigations. Law Enforcement would have been mightily remiss had they not used rapidly evolving, ubiquitous, and now firmly entrenched Social Media as a means, sometimes the only means, of connecting individuals. Social Media is not only used to solve crimes, but to prevent them.
The first Social Media website of historical note, Friendster, adopted the naming convention of peer to peer network, Napster, which was used to “share” music without payment. Napster was in full swing when 9/11 occurred, having gone live in 1999. As expected, Napster ran afoul of U.S. Copyright Laws and shut down in 2002.
Friendster picked up where Napster left off minus the music, leaving just the social connections. When Friendster.com went live in 2002, 3 million users signed on within the first few months. Social Media had taken off.
Myspace went live two years after the 9/11 attacks in 2003. The Facebook Website was launched in 2004. However, unbelievable it may seem today, from 2005-2009, Myspace was the largest social networking site in the world, and in June 2006 surpassed Google as the most visited website in the United States. Twitter was created in 2006 and now has over 300 million users.
Instagram started as a free mobile app on the Apple Platform in 2010. Two years later, Instagram already had 100 million active users. That same year Zuckerberg announced to the media at the start of October 2012 that Facebook had passed the monthly active users mark of one billion. Facebook acquired Instagram in April 2012 for a Billion US Dollars. As of December 2016, Instagram had 600 million active users.
As of the date of this post, Facebook has nearly two billion active users worldwide. As of this writing, the entire global population is seven billion. Facebook’s saturation goes well past just the U.S. Population (400 Million).
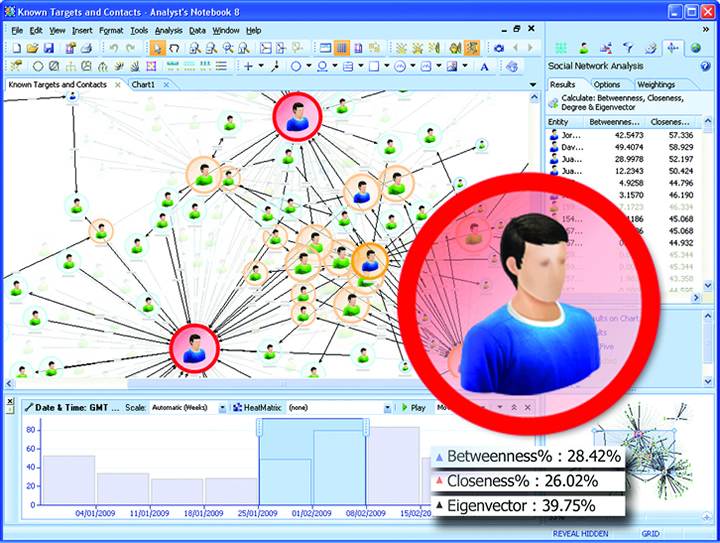
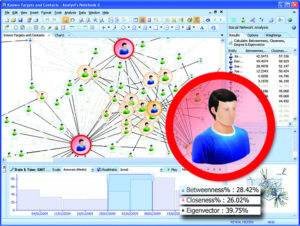
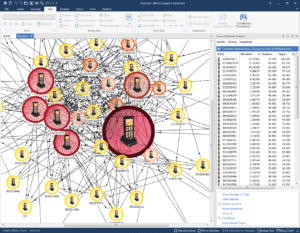
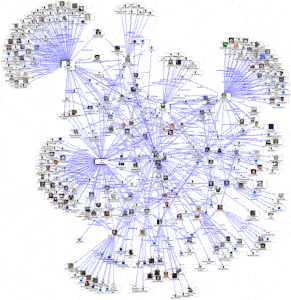
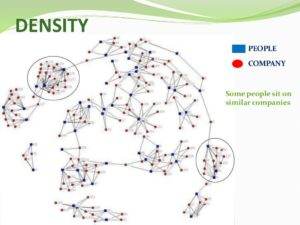
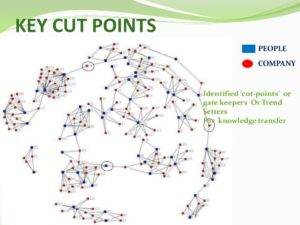
It’s no surprise that the government stalks you on Facebook, but not too many understand the depth and breadth of analysis, both manual and automatic, the government conducts in analyzing individuals, groups, organizations and even Nation States. Thus, the following is presented as a snapshot.
Abridgement of rights occurs in small doses. American Citizens should be wary.
Social_Media_Surveillance_and_Law_Enforcement 2015
Social Media Investigation – Chain of Custody and Authentication
cops= Social Media and Tactical Considerations for LE 2013
HISTORICAL ARTICLES (PRE 2017)
Are all Phone Calls and Emails Recorded and Available to the Government?
Are all Phone Calls and Emails Recorded and Available to the Government?
IMMIGRATION WILL EXAMINE YOUR FACEBOOK ACCOUNT
In a memo penned in 2008, the Department of Homeland Security’s U.S. Citizenship and Immigration Services described the goldmine of personal information to be found on online social networks and instructed agents how to take advantage of people’s “narcissistic tendencies” to sniff out fraud.
Huffington Post Article, “Fake Friends Adding Fresh Danger to Facebook”
Huffington Post: REVEALED: How Your Data Could Be Classified As ‘Terrorist Information’
Huffington Post: National Counterterrorism Center’s ‘Terrorist Information’ Rules Outlined In Document
NEW YORK — A training document released in response to a civil liberties organization’s lawsuit and obtained by The Huffington Post reveals that the government considers an “analyst’s wisdom” the ultimate arbiter of whether data on American citizens can be classified as “terrorist information” and retained forever.
“Only a CT (counter-terrorism) analyst can determine whether data constitutes terrorism information,” the electronic training course for new National Counterterrorism Center analysts states. “There is no requirement that the analyst’s wisdom be rock solid or infallible.”
The document, identified by its introduction as a “rules of the road” course on data access and use, is marked “SECRET.” But it was released in a significantly redacted form to the Electronic Privacy Information Center under a Freedom of Information Act request on Tuesday, in response to a lawsuit filed in August 2012.
The training course is a novel window into the thought processes of analysts for the NCTC, which was created by President George W. Bush in 2003 in response to recommendations from 9/11 Commission. The NCTC is supposed to connect the dots on potential terrorist threats to the United States by combining information from other agencies like the Central Intelligence Agency, Federal Bureau of Investigation and Department of Homeland Security.
The NCTC saw its powers to legally examine and retain data on American citizens and other people in the country vastly expanded under rules approved by the Justice Department in March 2012. As the Wall Street Journal reported in December, the agency can now copy entire databases — such as citizens’ flight records — and retain that information for up to five years.
The public affairs department of the Office of the Director of National Intelligence said in a written comment that the training document was created in 2012 and is still in use.
Since deeming data “terrorist information” makes it eligible to be saved in the NCTC’s database forever, the document’s fuzzy definition of terrorist information is a source for concern, said Ginger McCall of EPIC.
“This is high stakes, because you’re talking about potentially being classified in connection with terrorism information,” she said. “The data can be retained indefinitely then. We don’t know all the parties that this data is shared with, or all the uses that are made of this data.”
The NCTC guidelines say that data can be retained indefinitely where there is a “reasonable and articulable suspicion” that it has something to do with terrorism. The training course provides for the first time an explanation of how analysts come to that conclusion:
The analyst must be able to explain the “math” (logic) on their analysis and how they arrived at their conclusion. This is the articulable portion of the standard.
The “math” or analysis must be prudent to the average counterterrorism analyst. This is the reasonable portion of the standard.
“They try to boil it down to math, as if this is an exact science,” said McCall. “It’s not an exact science, as they acknowledge below.”
Further down on the same slide, the course states that “The totality of the facts — even if the facts individually appear innocent in nature” can be used to classify data as terrorist information. And it also states the line about there being “no requirement that the analyst’s wisdom be rock solid or infallible,” adding, “In fact, it is expected to change as new information comes to light.”
The document does not specify what kind of access the NCTC has to Americans’ private information. Before the center’s new guidelines went into effect, a Department of Homeland Security privacy official warned that they represented a “sea change” in how the government treated its citizens’ privacy.
An information paper released by the Office of the Director of National Intelligence in January claimed that the new guidelines improved on old ones by “adding specificity on how data is obtained, retained, and disseminated, and providing for enhanced safeguards and oversight mechanisms to protect important privacy and civil liberties.”
EPIC’s ultimate goal with its Freedom Of Information Act request is to find out which government agencies are sharing information with the NCTC, and under what terms they are allowing the center to make wholesale copies of databases. So far, however, the government has refused to provide the memorandums of understanding between the NCTC and other government agencies. The government claimed to EPIC that it couldn’t find any such memoranda, even though they are referenced and linked in the training guide. The ODNI public affairs office declined to comment on the missing memoranda, citing EPIC’s ongoing lawsuit.
Until the interagency agreements are released, McCall said, the public will remain in the dark.
“If we’re going to be using these sorts of mechanisms where it’s wholesale retention of information … we should have a real conversation about that,” she said. “We should have a real debate about what these protections for privacy and civil liberties are.”
Read the full document:
National Counterterrorism Center Analyst Training Guide
Immigration tactics aimed at boosting deportations
USA TODAY: Immigration tactics aimed at boosting deportations